Hi! I’ve been wanting to give SeaTable a try but unfortunately I can’t get it to work.
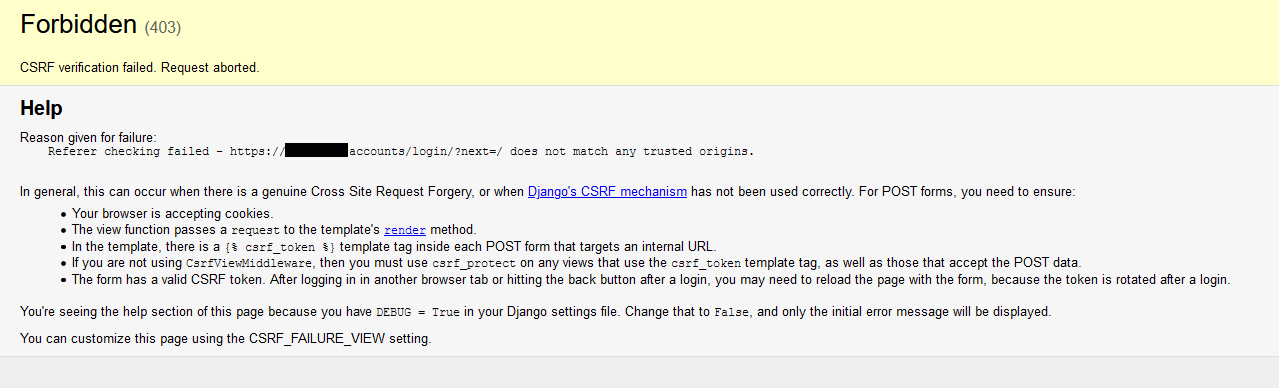
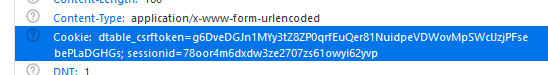
I want to use SeaTable without the automatic LetsEncrypt certificate feature because I will be proxying it through my frontend Nginx instance which already has a certificate. After following the steps in the documentation (Redirecting...) and setting up my reverse proxy configuration (see below), I get a Django CSRF validation error.
- I’ve tried to replace
http://withhttps://indtable_web_settings.pyandccnet.conf(and restarting Seatable service or container, both ways) but it did not help. - I’ve tried adding
mydomainindtable_web_settings.pyunder a newCSRF_TRUSTED_ORIGINSoption, but it did not succeed either. The DjangoDEBUGoption also didn’t give me any substantial hints (just saying thatmydomainisn’t a trusted origin). - I’ve also tried to use it with
SEATABLE_SERVER_LETSENCRYPT=True(after removing all containers and bind mounted directories), but I hit the same issue as in https://forum2.seatable.io/t/seatable-1-8-developer-edition-docker-fresh-installation-broken/461 (where you get[...] open() "/etc/nginx/sites-enabled/default" failed [...]in the seatable logs) and I could not get it to work as per the answers (that is, making sure that it is set toTruewhen the containers are initially created).
Thanks for any help,
Niklas
My docker-compose.yml:
version: '2.0'
services:
memcached:
image: memcached:1.5.6
entrypoint: memcached -m 256
restart: unless-stopped
db:
image: mariadb:10.5
environment:
- MYSQL_ROOT_PASSWORD=REDACTED
- MYSQL_LOG_CONSOLE=false
volumes:
- ./seatable-db:/var/lib/mysql
restart: unless-stopped
redis:
image: redis:5.0.7
restart: unless-stopped
seatable:
image: seatable/seatable:2.1.0
ports:
- "127.0.0.1:12001:80"
volumes:
- ./seatable-data:/shared
environment:
- DB_HOST=db
- DB_ROOT_PASSWD=REDACTED
- SEATABLE_SERVER_LETSENCRYPT=False
- SEATABLE_SERVER_HOSTNAME=mydomain
- TIME_ZONE=Europe/Berlin
links:
- db
- memcached
- redis
restart: unless-stopped
My reverse proxy configuration:
server {
server_name mydomain;
listen 80;
listen 443 ssl http2;
include i.d/acme.conf;
if ($scheme = http) {
return 302 https://$server_name$request_uri;
}
client_max_body_size 512M;
location / {
proxy_pass http://localhost:12001;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $server_name;
proxy_set_header X-Forwarded-Proto $scheme;
}
}